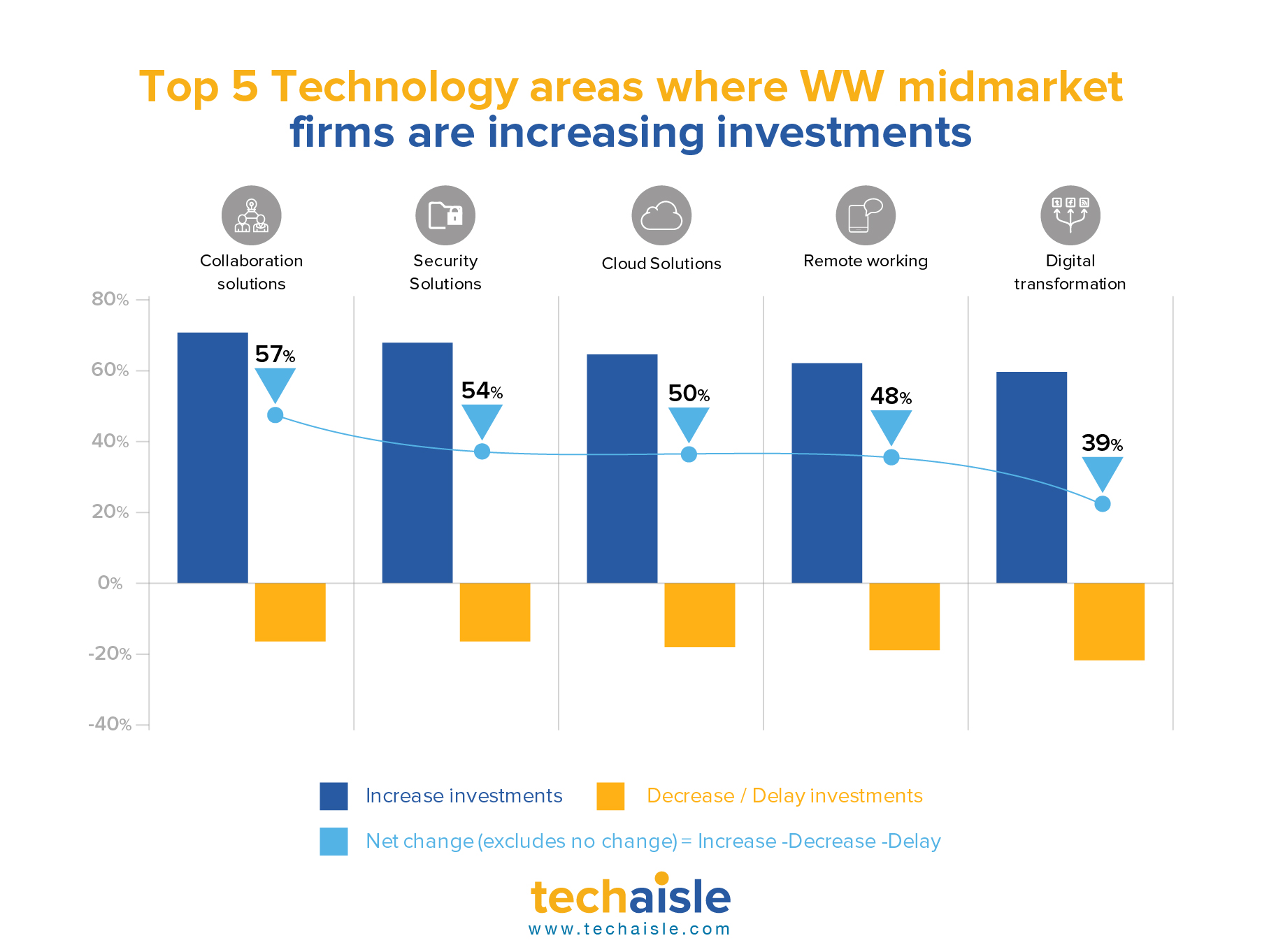
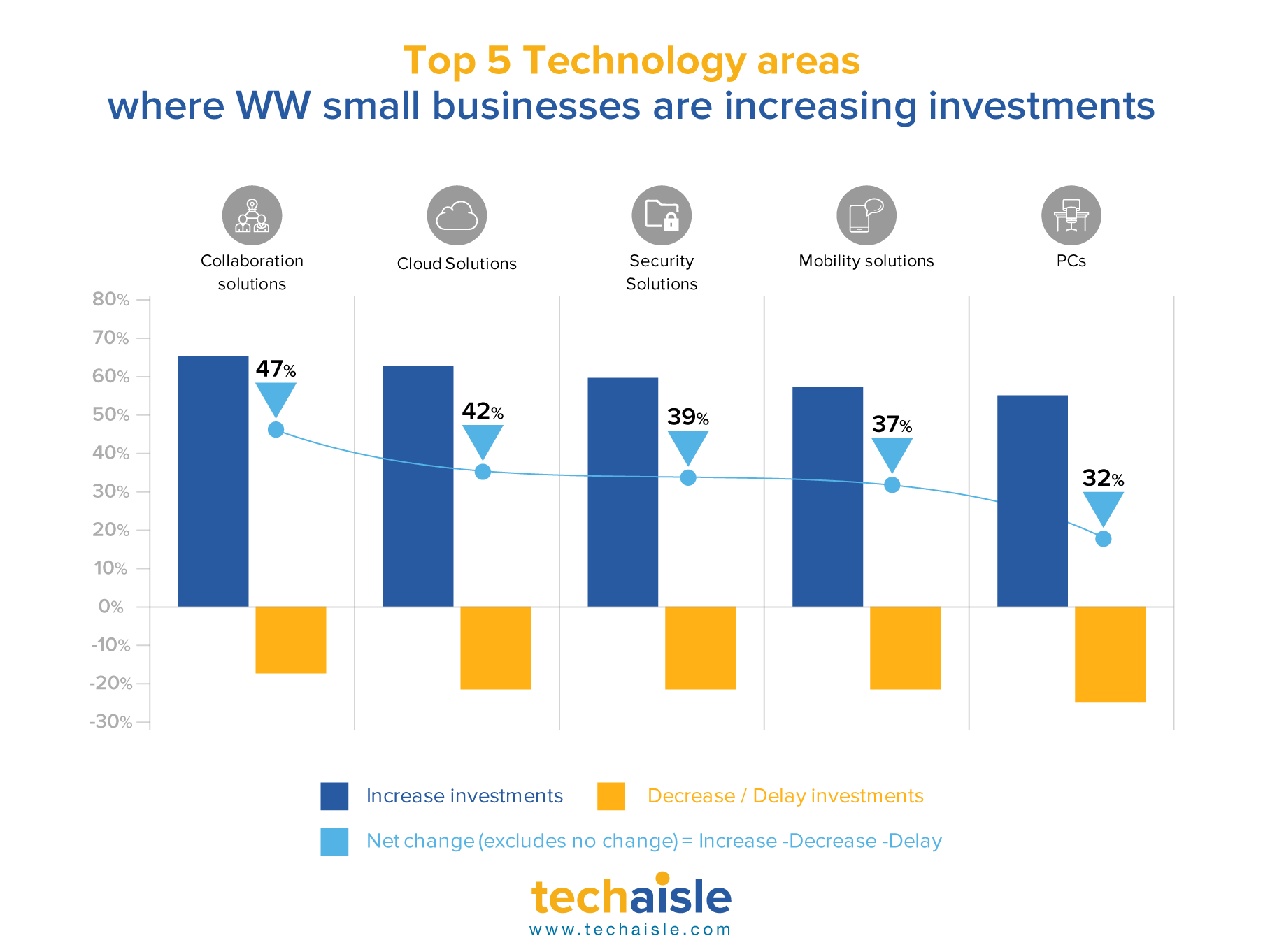
It is no secret that Cisco has made several attempts and investments to address the needs of small businesses. It would not be out of place to quote an English proverb that states: "A cat has nine lives. For three he plays, for three he strays, and for the last three he stays". This time I believe that Cisco will stay. Cisco has landed at a good place.
Today at Cisco Live 2020, Cisco unveiled latest updates to its Cisco Designed portfolio of small business solutions that are aligned with top five problems that Cisco is solving for small businesses.
- Work from home: how to meet and collaborate with employees and customers securely
- Cybercrime protection: how to safeguard from identity theft, hackers and internet attacks
- Always-on business: how to provide easy installation and reliable IT services using cloud technology
- Workplace monitoring: how to enable safe social distancing and real time monitoring
- New office: how to improve productivity and security at shared physical workspaces
The announcements
- Cisco Business Switches and Dashboard - easy to set up, secure connectivity for small businesses which are powering connections across remote and in-office workforce. The two new series of switches – CBS 250 Smart Switch and CBS 350 Managed Switch - provide essential functionality along with advanced security options and are priced right – starting at US$200 - for small businesses. Both switches support PoE+ and have integrated DoS protection and time-based ACLs. The switches are stackable and come with limited lifetime warranty (usually unheard of). Techaisle small business research on buyer care-abouts for technology solution selection supplier shows that price (67%), reliability (66%) and support (54%) are ranked top 3 criteria. Cisco switches are purpose-built to appeal to the care-abouts. The dashboard, which directly integrates with the switches, is a network management tool with a streamlined user interface (a “single pane of glass” for all Cisco devices that eliminates the need to work with Cisco’s command line interface) to manage entire network with integrated lifecycle management and automated alerting. With zero-touch plug and play deployment, and hosted in the cloud or on premises, it allows small businesses to set-up, monitor and operate network devices from a simple interface on any device.
- Tools to manage network in the Cloud – Cisco Meraki Health and Meraki Insight allows small business customers to monitor all aspects of their network and applications from Meraki Dashboard and API as well as detect and fix issues in minutes. As per Techaisle’s managed services research only 4% of small businesses have internal full-time IT staff and even within the 20-249 employee size segment, less than half are staffed with internal IT. Regardless of the size of IT staff, 79% of their time is spent on support and maintenance, majority in troubleshooting which creates not only IT efficiency deficit but also negatively impacts organizational productivity. Meraki Health’s objective is to make troubleshooting simple for the lean and almost non-existent and over-burdened small business IT staff.
- Cloud Mailbox Defense for Office 365 – enhanced email security solution, designed for use with Office 365, with no changes to mail flow or DNS and can be made operational with 5 minutes. O365 (renamed to M365) adoption is on a meteoric increase. For example, Techaisle research shows that 48% of US small businesses are planning to use M365 within the next year. However, a vast majority of small businesses worry about malware and phishing attacks, password compromise and account hijack. Only 3% of very small businesses and 27% of small businesses have internal full-time IT security staff. These small businesses usually fail to add a secure email gateway, because they are unable to manage operational overhead and lack expertise to change mail flows and operate complex policies. They prefer a solution that can be easily deployed and managed. Powered by Cisco Talos threat intelligence, Cloud Mailbox Defense, runs natively in MS Azure, can be plugged into O365 with minimal policy configuration and does not require any specialized training to manage. Minimum seat count to get started is 25.
- Webex Work bundle - a complete cloud collaboration solution that combines Webex Calling, Meeting and Messaging services in a single subscription, with attractive flexible monthly pricing for small businesses - per user/per month Webex licenses starting at $19.95/month. Techaisle research shows that within small businesses collaboration adoption efforts are being driven by demands for decision agility, speed of innovation, customer intimacy and faster time to market. 47% of small businesses are increasing investments in collaboration solutions because a lack of teamwork is impacting productivity. While the creation of a central information repository was the most important business driver for collaboration solutions initially, new adopters want to address the needs of increased employee mobility, dispersed team members and ad hoc scheduling.
Techaisle Take
To understand the profundity of Cisco’s small business solutions let us harken back to three of the top 10 SMB predictions I had written in 2015:
- Collaboration becomes a much bigger concept. In years past, “collaboration” was a big-company issue in which IT professionals used something called “presence” to connect staff to each other. What a quaint time that was! In 2015, I had said that this concept of collaboration will be swept into the dustbin of history. and it will become clear that collaboration spans files and people, staff and customers. It includes file exchange and multi-point editing; it extends beyond the corporate staff (and as a result, beyond large enterprises) to include customers; it has broken through the corporate walls, and demands support for mobility. In fact…
- Collabmobilicloud becomes an SMB management reality. There is a tendency in the press and in vendor product literature to treat collaboration, mobility and cloud as separate solutions. There is a tendency from the user perspective to treat them as aspects of a single approach to accessing, working with and sharing information. The users pay the bills, and in 2015, their perspective will predominate. Collaboration initiatives are part of mobility strategies, mobility is at the core of collaboration initiatives, and both are dependent on the cloud. This will have a major impact on application development and…
- Connected security becomes “security”. At one point, there was a debate in the security world - what was better – unified threat management (UTM) systems that ensured that there are no cracks between security products, or best-of-breed (BoB) products that could evolve as quickly as the threat landscape itself? BoB won that debate decisively; in fact, what used to be called “UTM” is now referred to as “next-generation firewalls,” one of many important “shields” around enterprise data, applications and users. However, with the expanding threat perimeter (caused in no small part by the trends towards hybrid and collabmobilicloud), 2015 is time to take a fresh look at how to ensure that all of the aspects of security infrastructure are integrated to protect against intrusion.
The above were true then and are even more poignant today. The Cisco Designed portfolio of small business-focused solutions directly addresses the needs and threat vectors for secure workplaces, better collaboration, simplified manageability and organizational productivity empowerment. Cisco has also made it easy for small businesses to buy the solutions, deploy and manage them either through their own internal staff or externally with the help of channel partners such as MSPs.
If the office of a small business is defined by devices, so too is the workplace defined by the ability to work from wherever those devices (and their users) are located. Small businesses are investing in mobility because it contributes to cost savings, increases market reach, improves productivity and establishes better ways of working. Security remains the top constraint for accelerating remote work adoption as small businesses struggle with data protection and mobile management. Techaisle global survey reveals that cloud, mobility, collaboration and security are among the top five technology priorities for over 60% of small businesses. 42% of small businesses are looking for solutions that are easy to buy, deploy, manage and support.
However, designing simplified products does not guarantee success in the small business segment. In an IT environment that is already very complex and likely to become more so, trusted advisors are very important to small businesses. Three quarters of small businesses rely on a trusted party – an internal employee with expertise in IT and/or external consultants – to provide advice on IT strategy. In most cases (over 60%), these advisors are trusted because they are viewed as unbiased and experienced, and able to provide the “right guidance” to the buyer. While the ‘unbiased’ observation would seem to rule out product vendors, small businesses exhibit a clear preference for advisors who can move seamlessly from advice to procurement and deployment. Cisco needs to invest in nurturing “super consultants”, both internally and externally (within channel partners) who can not only advise but also architect, deploy, manage and support Cisco Designed for Business portfolio solutions.
Regardless of the thoughtfully designed solutions, they are still discrete and transactional offerings. But we are increasingly immersed in a post-transactional market, where discrete sales of individual products or integrated systems are being replaced by agreements to provide IT functionality “as-a-Service.” Inexorably, the market is shifting from one defined by discrete purchase-and-deploy deals aligned with refresh cycles to one where businesses take a ‘hybrid IT’ approach that blends a limited number of on-premise assets with a growing range of on-demand services. To participate in this shift and stay relevant Cisco needs to create bundled solutions, including managed services with a recurring “as-a-service” offering.
Cisco should plan a larger product vision that aligns with digital transformation trends within small businesses. The vision should cover technologies such as HCI, SD-WAN, security, IoT, and workspaces. These integrated solutions will create reasons for small businesses to remain connected with Cisco.
Cisco has landed at a good place, finally. And it is ready to take off and soar within the small business segment. (Don’t muck it up)
Download the full pdf report here